How Does a Block of Data on a Blockchain Get Locked?
Written by
Maryam Aslam
Last Updated: May 30, 2025

Your Blockchain Journey Starts Here
Whether you're launching a DeFi platform, NFT marketplace or enterprise blockchain solution, we deliver technology that transforms. Book Your Free Consultation Today.
Blockchain technology functions as a decentralized ledger that ensures accuracy, transparency and security across various blockchain networks. It has significantly transformed how data is stored and secured. By offering high levels of integrity and transparency, it prevents unauthorized tampering by locking data within cryptographically secured blocks.
This locking mechanism preserves the immutability of information. The process relies on cryptographic hashing and consensus protocols, which make unauthorized changes nearly impossible. These features are particularly crucial for industries such as finance, legal and supply chain, which often rely on blockchain development to safeguard sensitive data.
An experienced blockchain development company is key to creating and maintaining secure blockchain-based systems. This helps businesses implement innovative solutions personalized to their needs. You can also opt to build your own, in-house blockchain development team, but that requires time and is usually more costly.
This article explains how the blockchain structure works, how blocks are added and locked, and how security is maintained across the network.
The structure of a blockchain block
Each block in a blockchain serves as a fundamental unit of data storage to provide transparency and be tamper-resistance. A typical block consists of the following components: data, nonce, hash and the previous block’s hash.
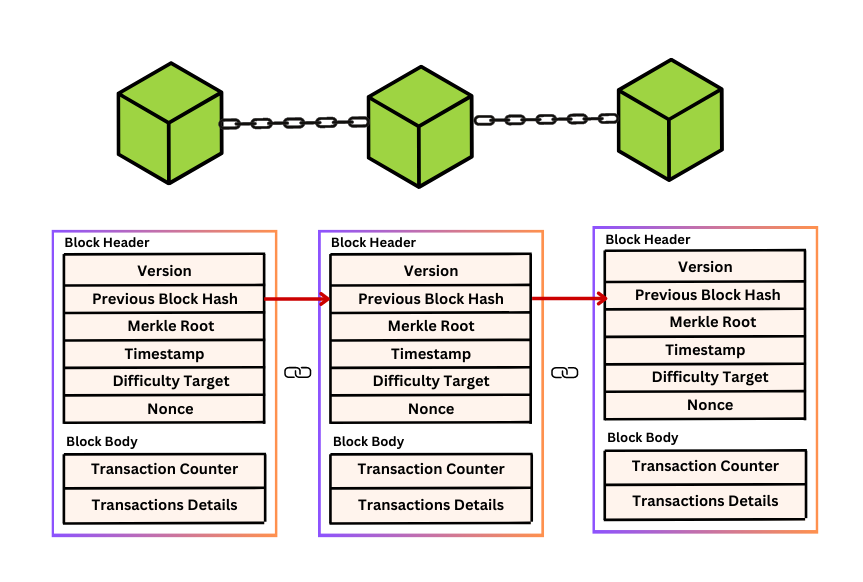
Source: blocktpoint.com
1. Data
Includes transaction details, smart contract logic and asset records.
2. Nonce
A randomly generated number used in Proof of Work blockchains, which miners manipulate to generate a valid hash.
3. Hash
A cryptographic signature unique to the block's data. Even minor changes to data will result in a completely different hash.
4. Previous block's hash
Links the current block to the one before it, creating a secure, chronological chain.
This structure makes sure that any tampering with a block breaks the entire chain to make blockchain networks extremely resistant to fraud.
The process of adding and locking a block
One of the core pillars of blockchain security is cryptographic hashing, a process that transforms input data into a fixed-length string of characters known as a hash. This hash functions as a unique digital fingerprint for that data. Even the slightest change in the original input drastically alters the hash output, immediately signaling that tampering has occurred. This one-way cryptographic function is essential for verifying data integrity without revealing the original information.
In practical application, Bitcoin’s blockchain offers a strong example. It structures transaction data using a Merkle tree, where each transaction is hashed and paired repeatedly until a single Merkle root is created. This root is then included in the block header. If even one transaction within that block is modified, the Merkle root and consequently the entire block hash changes. This disruption invalidates the block and alerts the network to maintain the integrity of the entire blockchain.
This tightly interwoven design makes it nearly impossible to manipulate past data without redoing all subsequent blocks, which would require enormous computational power. Such a system provides tamper-evident, verifiable records which makes blockchain an ideal solution for industries that require high levels of trust and transparency, especially when backed by a professional blockchain development services provider that works on these solutions around the clock.
Role of consensus mechanisms in locking a block
Consensus mechanisms are foundational to blockchain’s decentralized architecture. They validate data and secure the chain without needing a central authority. A professional blockchain app development process will often incorporate the most suitable consensus mechanism depending on the project's goals.
1. Proof of Work (PoW)
Miners solve complex mathematical puzzles to validate transactions and add blocks. It’s highly secure but energy-intensive, which makes it suitable for networks like Bitcoin where maximum security is a priority.
2. Proof of Stake (PoS)
Validators are chosen based on the amount of cryptocurrency they stake. It’s more energy-efficient than PoW and ensures that participants have a financial incentive to act honestly.
3. Delegated Proof of Stake (DPoS)
Token holders vote for a small group of delegates who validate blocks. This makes the process faster and more scalable, ideal for networks needing high transaction speed with some degree of decentralization.
These mechanisms make sure that only verified, trusted data gets added to the blockchain. By applying these during blockchain app development, businesses can operate with high levels of trust and accountability.
Security features that prevent data tampering
Blockchain’s reputation for tamper resistance stems from a combination of advanced cryptographic techniques and architectural principles designed to protect data at every stage. Here are the core features that enable this level of security:
1. Cryptographic hashing
Every piece of data stored on the blockchain is converted into a unique hash using cryptographic functions. Even the smallest change in the original data generates an entirely different hash. Since each block contains the hash of its contents as well as the hash of the previous block, any tampering immediately becomes evident, breaking the chain’s integrity. This makes unauthorized changes not only easy to detect but nearly impossible to execute undetected.
2. Immutable chain structure
Blockchain’s linear, chronological structure ensures that once a block is added to the chain, altering it would require modifying every subsequent block across all nodes in the network. This would demand an extraordinary amount of computing power and coordination, especially in large, distributed systems. The immutability of this structure is central to blockchain’s value in maintaining long-term, trustworthy records.
3. Consensus protocols
Protocols like Proof of Work (PoW), Proof of Stake (PoS) and Delegated Proof of Stake (DPoS) require nodes in the network to agree on the validity of transactions before a block is added. This distributed agreement ensures that no single entity can manipulate the blockchain. It also helps prevent fraud, double-spending, or the addition of invalid data, reinforcing trust across decentralized systems.
4. Digital signatures
Each transaction on the blockchain is authenticated using digital signatures based on public-key cryptography. These signatures verify that the transaction was initiated by a legitimate party and that its contents have not been altered. This guarantees both data integrity and origin authentication, which is vital for securing sensitive information.
5. Merkle trees
Merkle trees structure transaction data within a block by recursively hashing pairs of data entries, ultimately producing a single Merkle root. This root summarizes all the transactions in the block. If any individual transaction is changed, the Merkle root will differ, alerting the system to the inconsistency. This structure makes verifying large datasets faster and more efficient while preserving data accuracy.
6. Timestamping
Each block includes a timestamp indicating the exact moment it was mined or added to the chain. This chronological marker prevents transaction replay, supports forensic auditing, and establishes a clear, verifiable sequence of events. Timestamping helps ensure consistency, detect anomalies and maintain the order of operations across the network.
Together, these layered security features create a powerful framework that prevents data manipulation, enhances traceability and ensures the transparency and reliability of the blockchain.
Conclusion
Blocks in a blockchain are locked and secured through cryptographic hashing, consensus mechanisms like Proof of Work or Proof of Stake, and linking each block to the previous one. These features ensure that data remains tamper-proof and transparent. The security of these mechanisms is crucial for maintaining the integrity, trust and decentralized nature of blockchain systems.
As blockchain technology continues to expand into major industries, the ability to securely lock and validate blocks will play a central role. Looking ahead, advancements in cryptography and consensus will further strengthen the reliability of blockchain-based applications.
FAQs
1. How does a block of data on a blockchain get locked? A block gets locked after its transactions are verified, grouped, and validated via consensus mechanisms like Proof of Work or Proof of Stake. It is then cryptographically linked to the previous block to provide data integrity.
2. How does blockchain secure data? Blockchain secures data using cryptographic hashing, decentralization, and consensus validation. Every block is chronologically linked to create a tamper-proof chain.
3. Can data be removed from the blockchain? No, blockchain data is immutable. However, outdated or incorrect entries can be rendered obsolete using soft forks or off-chain storage which preserves the chain's integrity without deleting past records.




