How Cryptographic Hashing Keeps Blockchain Safe
Written by
Nabia Hassan Sabzwari
Last Updated: May 30, 2025

Your Blockchain Journey Starts Here
Whether you're launching a DeFi platform, NFT marketplace or enterprise blockchain solution, we deliver technology that transforms. Book Your Free Consultation Today.
Blockchain’s inherent features like transparency, immutability and mechanisms like proof of work and cryptographic hashes add up to its robust security. Blockchain hash mechanisms are vital to maintaining data integrity, it does this by verifying data in the document to check if it was tampered or changed in any way.
A hash function generates a unique value through a cryptographic algorithm, which then matches the received data to confirm its authenticity. This prevents unauthorized changes, making it a crucial component in blockchain development. Let’s explore how this function works and its role in securing blockchain.
What is a hash function in blockchain?
Even if you're new to Web3, you may have encountered hashing in cybersecurity—for example, when websites store user passwords as hashed values rather than plain text. If you set a password like ‘hello123,’ a hash function converts it as follows:
hello123 → 5d41402abc4b2a76b9719d911017c592
Even a minor change, like ‘Hello124,’ generates a completely different hash, demonstrating hashing’s sensitivity to input variations.
In simple terms, a hash function is a mathematical algorithm that converts input data (usually a string of letters and numbers) into a fixed-length output.
In blockchain development, hashing secures transactions and links blocks within the chain. When a transaction occurs, its details (such as sender, receiver, and amount) are passed through a hash function like SHA-256 or Keccak-256, generating a unique, fixed-length output.
Example of blockchain hashing
Transaction Data → Alice → Bob: 2 BTC
Timestamp → 1700000000
SHA-256 Hash →
b6f6991d1bcd9c5f3caa738a5b7b23ee2f2f2335dfb9f063d013ab9873ff8e4d
Key properties of hashing
Deterministic → The same input always produces the same hash.
Irreversible → The original data cannot be derived from the hash.
Collision-resistant → No two different inputs generate the same hash.
How hashing secures blockchain transactions
Hashing functions assign a unique digital fingerprint to each transaction. When data is processed through a hash function (like SHA-256), it generates a fixed-length hash. Even the slightest change in data results in an entirely different hash, making tampering immediately detectable.
How hashes link blocks
Each block in a blockchain contains:
Transaction information
The hash of the previous block
New hash for current block
Since each new block references the previous block’s hash, they form an interdependent chain. If a hacker tries to modify any data, the corresponding hash changes, breaking the entire chain and making alterations practically impossible.
How hashing is used in Proof-of-Work (PoW)
Proof-of-Work (PoW), used in Bitcoin, requires miners to solve complex mathematical puzzles using hashing. Miners repeatedly hash block data with different numbers (nonces) until they find a hash that meets a predefined difficulty target. The first miner to do so adds the block to the chain and earns a reward. This process makes network attacks extremely costly and nearly impossible.
How hashing is used in Proof-of-Stake (PoS)
In Proof-of-Stake (PoS), used in Ethereum 2.0, validators are selected based on the amount of cryptocurrency they stake as collateral. Hashing ensures fairness by randomly selecting validators while maintaining network security and consistency.
The role of hashing in blockchain development
One essential tool for blockchain development is hashing, which strengthens data accuracy, security,and reliability. For data verification, developers use hashing to assign a distinct hash to every transaction or block.
This allows for quick validation without storing entire datasets since even minor changes to the data produce entirely different hashes, signaling tampering.
Hashing protects private data, including user credentials, contract states and transaction logs in smart contracts and decentralized applications (dApps), preventing unauthorized access.
It plays a key role in security, enabling private blockchains to regulate data access within permissioned networks and supporting public blockchains in consensus mechanisms like Proof-of-Work (PoW) and Proof-of-Stake (PoS).
To verify data, secure transactions, and prevent fraud or double-spending, blockchain developers apply hashing through cryptographic algorithms such as Blake2b, Keccak-256, and SHA-256.
Practical applications of hashing in blockchain
The Ethereum and Bitcoin networks depend on hashing algorithms to validate transactions.
Bitcoin uses the SHA-256 algorithm to hash transaction data, assigning each transaction a unique identifier. To add new blocks and validate transactions, miners compete to solve complex mathematical puzzles based on these hashes. This process is known as Proof-of-Work.
Similarly, Ethereum applies the Keccak-256 (SHA-3) algorithm to hash smart contracts and transaction data, maintaining data accuracy and enabling secure execution on its decentralized platform.
In blockchain development, digital signatures rely on hashing to uphold the integrity and authenticity of transactions. When a user initiates a transaction, the details are hashed and then encrypted using the sender’s private key to generate a digital signature.
To confirm authenticity, the recipient decrypts the signature using the sender’s public key. This mechanism ensures the transaction is valid and originates from the stated sender, reinforcing the security of blockchain communications.
By using hashing to maintain data accuracy, businesses increasingly turn to blockchain technology for safe record-keeping. Documents such as financial transactions, supply chain logs and court records are hashed and stored on the blockchain. Any modification to the original data results in a mismatch with the stored hash, instantly revealing potential tampering. This unchangeable recordkeeping is essential for compliance audits and ensuring the reliability of critical data.
Hashing is also applied in identity verification systems based on blockchain technology to protect personal data. Instead of storing actual sensitive information, only the hashed version is recorded on the blockchain.
When verifying an individual’s identity, the provided data is hashed and compared to the stored hash. If they match, the identity is confirmed, without exposing personal details. This approach increases security while giving users greater control over their personal information.
Innovations & trends in blockchain hashing
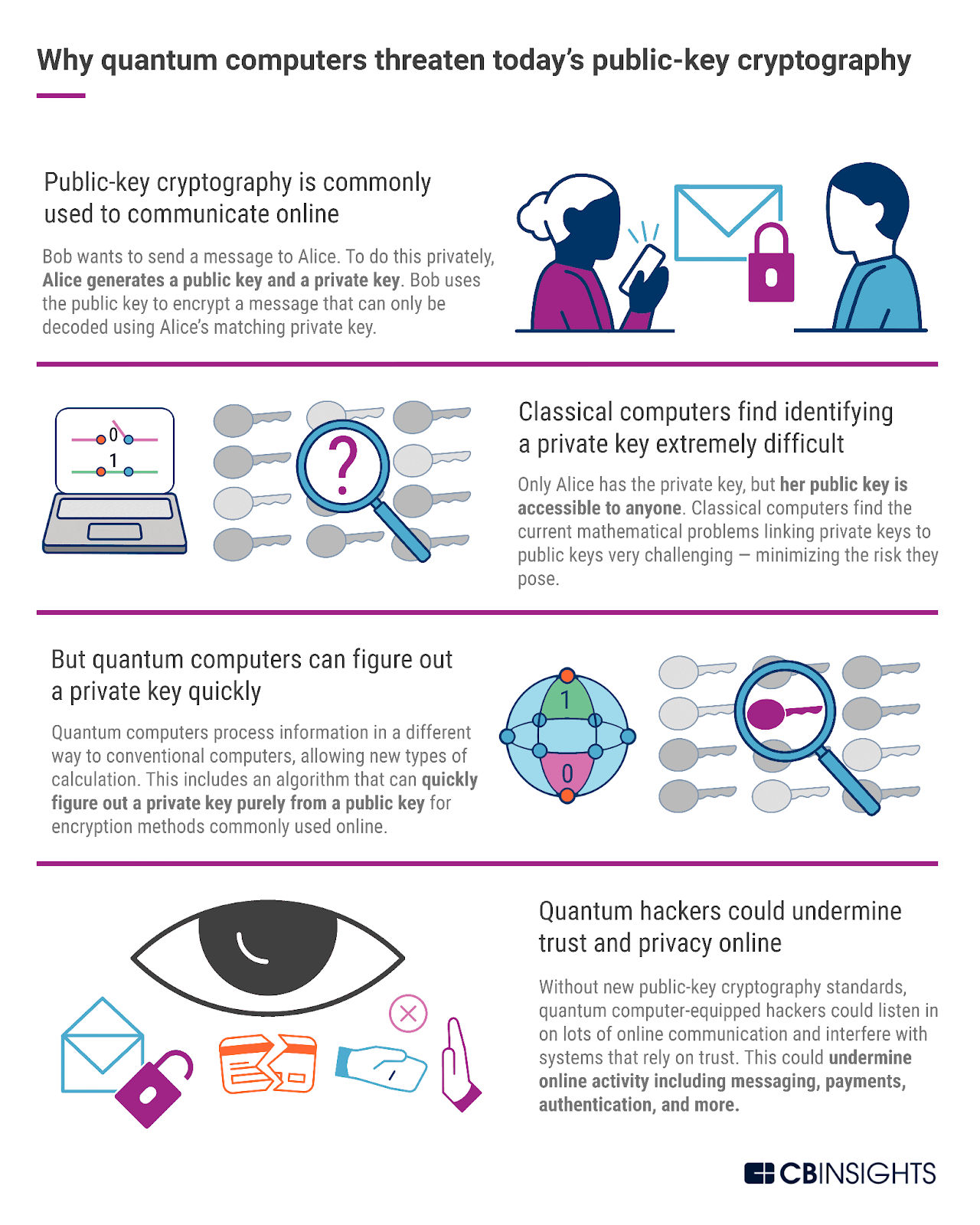
The demand for hashing algorithms with enhanced security and performance is rising as blockchain applications become more widespread. One of the best blockchain development trends is the creation of quantum-resistant hashing algorithms, designed to protect blockchain systems from potential threats posed by quantum computing.
With the efficiency needed for blockchain operations, these new algorithms seek to offer strong security. Any blockchain development company is constantly improving hash-based security measures. One way to achieve this is by using hybrid hashing techniques which combine several algorithms to reduce the risk of single points of failure.
Concerns about the environment related to blockchain mining operations are also being addressed by attempts to optimize hashing procedures to use less energy. To guarantee security and effectiveness hashing in blockchain systems must be implemented according to industry best practices.
This entails changing cryptographic protocols frequently to fend off new threats, choosing hashing algorithms that are suitable for the applications particular security needs and carrying out thorough security audits to find and fix vulnerabilities. Maintaining strong blockchain ecosystems also requires putting a strong emphasis on educating and training developers in secure coding techniques.
The use of sophisticated hashing techniques is expected to improve blockchain security in the future. Post-quantum cryptography research is accelerating with the goal of creating hashing algorithms that can withstand quantum computer attacks.
The overall security framework of blockchain networks can be strengthened by improving the detection of fraudulent activity and streamlining consensus processes through the integration of artificial intelligence and machine learning with hashing processes.
Traditional blockchain cryptography vs. quantum cryptography
| Feature | Traditional Cryptography | Quantum Cryptography |
|---|---|---|
| Algorithms used | SHA-256, RSA, ECDSA | Quantum Key Distribution (QKD) |
| Security basis | Relies on mathematical complexity (factoring, discrete logs) | Based on quantum mechanics (superposition, entanglement) |
| Vulnerabilities | Susceptible to quantum attacks (e.g., Shor’s Algorithm) | Resistant to quantum-based threats |
| Key exchange | Uses public-private key pairs (asymmetric encryption) | QKD enables secure, unbreakable key exchange |
| Tamper detection | Hashing (Merkle trees, digital signatures) | Quantum principles detect interference (measurement disturbance) |
| Real-world use cases | Widely adopted in Bitcoin, Ethereum and enterprise blockchains | Still experimental, mainly used in high-security communications |
Conclusion
Hash functions play a fundamental role in blockchain security, ensuring immutability, authentication, and data integrity. As blockchain tech expands across industries, adopting advanced hashing techniques becomes essential. Organizations utilizing blockchain solutions must prioritize strong hashing mechanisms to protect sensitive data, maintain transactional integrity and build user trust. Staying informed on advancements in cryptographic hashing and adhering to industry best practices will be key to securely using blockchain’s full potential.
For businesses seeking expert blockchain development services, Pixelette Technologies offers expert services in building secure, scalable, and high-performance blockchain systems.




